|
A pretty big flaw has been release under CVE-2016-5195 that allows a privilege escalation attack in the Linux Kernel that has been there since 2007. The conditions are almost impossible to reach in normal operations but some programs have been released to force those conditions by using two threads.
To reproduce it: 1. Download the dirtyc0w.c file from https://github.com/dirtycow/dirtycow.github.io 2. Compile it using gcc for example: gcc -pthread dirtyc0w.c -o dirtyc0w 3. Use it as follow: ./dirtyc0w <file_to_modify> <new_file_content> 4. Obviously, thanks to Dirty Cow, the <file_to_modify> can be a file on which the user does not have permission to modify, including root files ! The flaw works by writing to memory the new content so you cannot write content longer than the original size. If you attempt to write "123456" to a file containing "456", it will write "123".
7 Comments
I recently installed Ubuntu 12.04.1 TLS on one of my servers running Windows Server 2008 R2, following a reboot BIOS was stuck with an error message indicated that no valid media was inserted that allowed it to boot.
I verified and re-verified boot order, no problem, hard drive was indeed detected and first in boot order. I put back the DVD reader and started the server with Ubuntu Live CD. I then noticed that the recently installed Ubuntu was indeed there and well installed by mounting the partition. Issue was with the Grub, to repair it using Boot Repair from Ubuntu Live CD: - Connect to the internet. - Open a terminal, add the repository and install boot-repair.
sudo add-apt-repository ppa:yannubuntu/boot-repair
sudo apt-get update sudo apt-get install boot-repair - Then start Boot Repair and choose ”Recommended repair”. - Remove the Live CD and reboot the computer, it will start correctly on the hard drive.
Following a Pause or a Stoppage of a virtual machine it's possible that the following message pops up:
Failed to lock main memory file [...]
If that is the case you can get ride of this error by deleting the folder <vm_name>.lck that is located where the virtual machine is stored. Then the virtual machine should start successfully.
Receiving error: 500.19 0x8007007e
"The requested page cannot be accessed because the related configuration data for the page is invalid." To fix this error do the following: Open a command prompt. Type in:
%windir%\system32\inetsrv\appcmd.exe set config -section:system.webServer/httpCompression /-[name='xpress']
If you need to enable it back:
%windir%\system32\inetsrv\appcmd.exe set config -section:system.webServer/httpCompression /+[name='xpress',doStaticCompression='false',dll='%windir%\system32\inetsrv\suscomp.dll']
After modifying a Cisco (router/switch) equipment's configuration it's possible that the configuration service of the equipment activates. This services will generate TFTP (Trivial File Transfer Protocol) broadcast requests on all interfaces of the equipment looking for a configuration on the network. It generates the following log message on the equipment:
- %Error opening tftp://255.255.255.255/network-confg - %Error opening tftp://255.255.255.255/cisconet.cfg - %Error opening tftp://255.255.255.255/3620-confg - %Error opening tftp://255.255.255.255/3620.cfg This service can be annoying if you have a TFTP server running on your network as it will try to reply to those requests ; moreover, it slows down equipment's boot time as it will wait for requests to be replied or time out to finish booting up. To disable that service use the following commands:
Router#config terminal Router(config)#no service config Router(config)#exit Router#copy running-config startup-config Source : Cisco official related page
If you have deleted the IOS in memory from a Cisco router and rebooted the router, it will started in ROMmon (ROM Monitor) mode.
Once you get ROMmon prompt, you will have to set some variable's values to be able to execute on IOS transfer from a TFTP server:
rommon 1 >IP_ADDRESS=10.0.0.1
rommon 2 >IP_SUBNET_MASK=255.0.0.0 rommon 3 >DEFAULT_GATEWAY=10.0.0.2 rommon 4 >TFTP_SERVER=10.0.0.2 rommon 5 >TFTP_FILE=c2800nm-advipservicesk9-mz.124-15.T1.bin rommon 6 >tftpdnld Once completed, use "reset" command to reboot the router. You can then make sure the IOS has been correctly transfered in flash memory using the following command:
Router#dir flash:
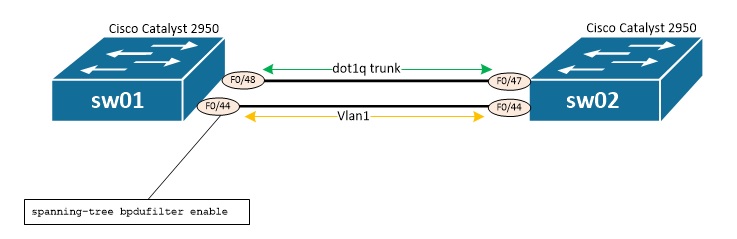
This tutorial demonstrates a potential looping risk introduced by BPDU filter.
Below is the lab architecture which will be used that include 2 Cisco Catalayst 2950.
Below are interesting configuration's parts of both switches:
hostname sw01 ! spanning-tree mode rapid-pvst spanning-tree portfast default no spanning-tree optimize bpdu transmission spanning-tree extend system-id ! ! ! ! vlan 3 name test ! vlan 1 name Management ! interface FastEthernet0/44 switchport access vlan 1 switchport mode access spanning-tree bpdufilter enable ! interface FastEthernet0/48 switchport mode trunk switchport nonegotiate speed 100 duplex full spanning-tree link-type point-to-point ! interface Vlan3 no ip address no ip route-cache ! interface Vlan1 ip address 192.168.200.11 255.255.255.0 no ip route-cache ! hostname sw02 ! spanning-tree mode rapid-pvst spanning-tree portfast default no spanning-tree optimize bpdu transmission spanning-tree extend system-id ! ! ! ! vlan 3 name test ! vlan 1 name Management ! interface FastEthernet0/44 switchport access vlan 1 switchport mode access spanning-tree portfast spanning-tree bpduguard enable ! interface FastEthernet0/47 switchport mode trunk switchport nonegotiate speed 100 duplex full spanning-tree link-type point-to-point ! interface Vlan1 ip address 192.168.200.12 255.255.255.0 no ip route-cache shutdown !
We see that the following configuration has been applied to F0/44 on sw01:
spanning-tree bpdufilter enable
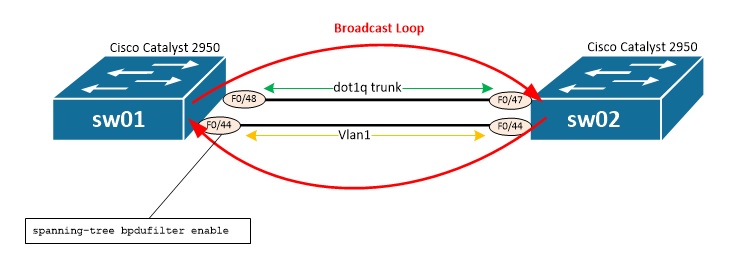
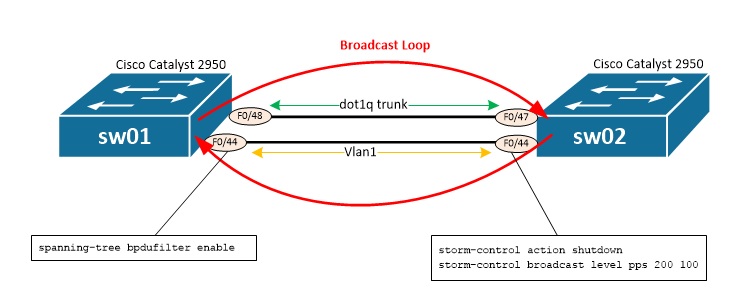
That configuration will actually prevent switches to detect the loop as there won't be anymore BPDUs sent and received on F0/44. By pinging, switch will send a broadcast ARP request to try and find the corresponding MAC address associated with the IP address. Yet, because of BPDU filtering applied to F0/44 of sw01 that broadcast will loop indefinitely between sw01 and sw02. sw01#ping 192.168.200.200 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.200.200, timeout is 2 seconds: ..... Below is the results of several show interface f0/44 and we note that traffic increases constantly on input and output (see input/output rate, Received X broadcasts): sw01#sh int f0/44 FastEthernet0/44 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0011.5c9c.0aac (bia 0011.5c9c.0aac) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, media type is 100BaseTX input flow-control is unsupported output flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:00, output 00:00:05, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 721000 bits/sec, 765 packets/sec 5 minute output rate 710000 bits/sec, 753 packets/sec 243451 packets input, 28715722 bytes, 4 no buffer Received 243321 broadcasts (262 multicast) 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 4 ignored 0 watchdog, 262 multicast, 0 pause input 0 input packets with dribble condition detected 244057 packets output, 28817529 bytes, 0 underruns 0 output errors, 0 collisions, 12 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 PAUSE output 0 output buffer failures, 0 output buffers swapped out ! sw01#sh int f0/44 FastEthernet0/44 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0011.5c9c.0aac (bia 0011.5c9c.0aac) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 4/255, rxload 50/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, media type is 100BaseTX input flow-control is unsupported output flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:00, output 00:00:04, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 20361000 bits/sec, 38952 packets/sec 5 minute output rate 1663000 bits/sec, 2118 packets/sec 14344973 packets input, 944363741 bytes, 13 no buffer Received 14344825 broadcasts (350 multicast) 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 13 ignored 0 watchdog, 350 multicast, 0 pause input 0 input packets with dribble condition detected 1022704 packets output, 102173564 bytes, 0 underruns 0 output errors, 0 collisions, 12 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 PAUSE output 0 output buffer failures, 0 output buffers swapped out ! sw01#sh int f0/44 FastEthernet0/44 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0011.5c9c.0aac (bia 0011.5c9c.0aac) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 3/255, rxload 73/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, media type is 100BaseTX input flow-control is unsupported output flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:01, output 00:00:05, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 28981000 bits/sec, 55975 packets/sec 5 minute output rate 1265000 bits/sec, 1613 packets/sec 23375847 packets input, 1522340144 bytes, 13 no buffer Received 23375691 broadcasts (390 multicast) 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 13 ignored 0 watchdog, 391 multicast, 0 pause input 0 input packets with dribble condition detected 1022713 packets output, 102174543 bytes, 0 underruns 0 output errors, 0 collisions, 12 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 PAUSE output 0 output buffer failures, 0 output buffers swapped out ! sw01#sh int f0/44 FastEthernet0/44 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0011.5c9c.0aac (bia 0011.5c9c.0aac) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 2/255, rxload 92/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, media type is 100BaseTX input flow-control is unsupported output flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:02, output 00:00:00, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 36803000 bits/sec, 71418 packets/sec 5 minute output rate 913000 bits/sec, 1165 packets/sec 34082686 packets input, 2207578307 bytes, 13 no buffer Received 34082521 broadcasts (439 multicast) 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 13 ignored 0 watchdog, 439 multicast, 0 pause input 0 input packets with dribble condition detected 1022725 packets output, 102176117 bytes, 0 underruns 0 output errors, 0 collisions, 12 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 PAUSE output 0 output buffer failures, 0 output buffers swapped out ! sw01#sh int f0/44 FastEthernet0/44 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0011.5c9c.0aac (bia 0011.5c9c.0aac) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 1/255, rxload 123/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, media type is 100BaseTX input flow-control is unsupported output flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:00, output 00:00:02, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 48623000 bits/sec, 94753 packets/sec 5 minute output rate 379000 bits/sec, 488 packets/sec 62325343 packets input, 4015110370 bytes, 13 no buffer Received 62325152 broadcasts (570 multicast) 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 13 ignored 0 watchdog, 570 multicast, 0 pause input 0 input packets with dribble condition detected 1022754 packets output, 102179585 bytes, 0 underruns 0 output errors, 0 collisions, 12 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 PAUSE output 0 output buffer failures, 0 output buffers swapped out ! sw01#sh int f0/44 FastEthernet0/44 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0011.5c9c.0aac (bia 0011.5c9c.0aac) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 4/255, rxload 135/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, media type is 100BaseTX input flow-control is unsupported output flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:02, output 00:00:02, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 53140000 bits/sec, 103711 packets/sec 5 minute output rate 1835000 bits/sec, 3534 packets/sec 101727727 packets input, 2241898068 bytes, 22 no buffer Received 101727498 broadcasts (766 multicast) 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 22 ignored 0 watchdog, 766 multicast, 0 pause input 0 input packets with dribble condition detected 3992664 packets output, 292256243 bytes, 0 underruns 0 output errors, 0 collisions, 12 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 PAUSE output 0 output buffer failures, 0 output buffers swapped out That problem can be fixed several ways: - Shutdown/no shutdown of port (yet if configuration and cabling remains the same the issue will re-occur quickly) - removing the loop by shutting down the port or unplugging the cable permanently - Changing spanning tree configuration (especially BPDU filter) - Apply a storm-control configuration What's next focuses on the last solution: applying storm-control configuration. Storm-control allows to define a limit, in PPS (Packets Per Second) or percentage along with an associated action to apply if the thershold is reached (send an alarm or shutdown port). Here we will shutdown the port to remove the loop. Storm-control is applied on a per-interface basis and must define a packet type (unicast, multicast, broadcast), a threshold at which an alarm is raised and a threshold at which switch will consider trafic is back to standards. Below is shown how storm-control is applied, then a ping is started, thus generating a brodcast (once again due to the ARP request generated by the switch in order to find the MAC address associated to the IP address); finally show storm-control broadcast allows to see storm-control's activities: sw02(config)#int f0/44 sw02(config-if)#storm-control action shutdown sw02(config-if)#storm-control broadcast level pps 200 100 sw01#ping 192.168.200.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.200.2, timeout is 2 seconds: 01:26:34: %STORM_CONTROL-2-SHUTDOWN: Storm control shut down FastEthernet0/44 01:26:35: %STORM_CONTROL-2-SHUTDOWN: Storm control shut down FastEthernet0/44. 01:26:36: %LINK-5-CHANGED: Interface FastEthernet0/44, changed state to administratively down 01:26:37: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/44, changed state to down.... ! sw01#sh storm-control broadcast | i ^Interface|Fa0/44 Interface Filter State Trap State Upper Lower Current Traps Sent Fa0/44 Shutdown inactive 200 pps 100 pps 0 pps 0 Instead of copy/pasting the content of the post, I am linking here a post to Cisco's support forum to a very useful post I found about Cisco's Access Points images naming convention: >> link here <<
If you need to call a URL from a Cisco router (example: call a Web Service which will send an email...) as you would do using a WGET on a UNIX or Windows computer, here are two ways of doing it:
1. Using an IP SLA
ip sla 10
http raw http://core-layer.com version 1.1 frequency 60 http-raw-request GET /script.html?param1=1 HTTP/1.1\r\n Connection: keep-alive\r\n Authorization: Basic YWRtaW46cGFzc3dvcmQ=\r\n \r\n exit The section http-raw-request will allow you to add HTTP headers if needed: for example, « Authorization: » header will allow the router to authenticate to the web page. That header si followed by authentication type (here « Basic ») and the string encoded in Base64: « username:password ». Which gives YWRtaW46cGFzc3dvcmQ= for admin:password . You can then start the SLA using ip sla schedule 10... 2. Using a TCL script The same kind of request can be created using a TCL script (saved in router's flash memory for example) and then directly called for the CLI with tclsh flash:script.tcl arg1 arg2 arg3 ... Here is an example of TCL script saved in flash:
source "tmpsys:lib/tcl/http.tcl"
set arg1 [lindex $argv 0] http::geturl " http://core-layer.com/script.html?param1=$arg1" -headers "Connection keep-alive Authorization \"Basic YWRtaW46cGFzc3dvcmQ=\"" Here are a couple comments on that script - Many TCL script examples will tell you to add the reference to http this way:
package require http
Yet, Cisco stores librairies in « tmpsys:lib/tcl/» hence the following command:
source "tmpsys:lib/tcl/http.tcl"
- To add HTTP headers you have to add parameter -headers which is then followed by headers formatted this way:
Header1 Value1 Header2 Value2 Header3 Value3 ...
So you should always have an even number of strings after parameter -headers . If a header requires a value with spaces in it you have to escape " using \" . |
Archives
July 2021
Categories
All
|
 RSS Feed
RSS Feed