|
I recently needed to hide the cursor upon boot in the GUI on a Raspberry Pi running Raspbian. I found the following method which is easy to install and works great.
Install Unclutter and edit the LXDE autostart script:
sudo apt-get install unclutter
nano ~/.config/lxsession/LXDE-pi/autostart Turn the cursor Off by adding the following line:
@unclutter -idle 0
Then you can reboot and cursor will disappear.
8 Comments
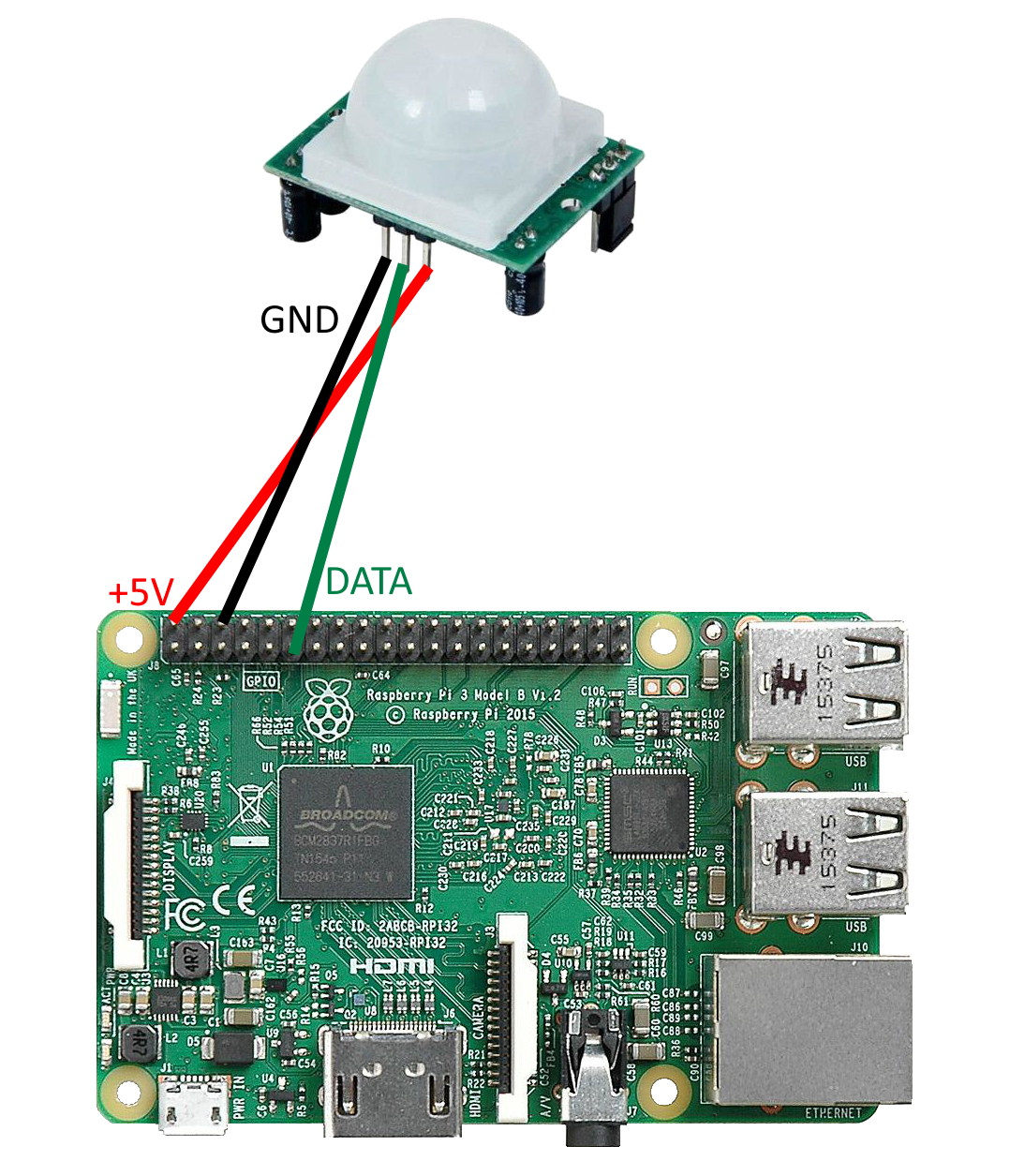
I recently purchased a PIR Detector HV-SR501 and here is a simple program to use it in Python with a Raspberry Pi 3.
Let's look at the wiring:
CAUTION: Verify on the PIR sensor's board that it has to be wired as displayed, the pinout on the PIR sensor is, on some models, inverted compared to the picture.
Once wired, below is a Python program that reads from the Raspberry Pi 3's GPIO ping #11 and prints every second if a movement has been detected.
import RPi.GPIO as GPIO
import time GPIO.setmode(GPIO.BOARD) GPIO.setup(11, GPIO.IN) while True: i=GPIO.input(11) if i==0: print time.ctime(),": no mouvement detected" else: print time.ctime(),": !!!!!!!!!! mouvement detected !!!!!!!!!!" time.sleep(1) You can change the two resistances on the other side of the PIR sensor using a screw driver to vary the delay and sensibility of the sensor. A pretty big flaw has been release under CVE-2016-5195 that allows a privilege escalation attack in the Linux Kernel that has been there since 2007. The conditions are almost impossible to reach in normal operations but some programs have been released to force those conditions by using two threads.
To reproduce it: 1. Download the dirtyc0w.c file from https://github.com/dirtycow/dirtycow.github.io 2. Compile it using gcc for example: gcc -pthread dirtyc0w.c -o dirtyc0w 3. Use it as follow: ./dirtyc0w <file_to_modify> <new_file_content> 4. Obviously, thanks to Dirty Cow, the <file_to_modify> can be a file on which the user does not have permission to modify, including root files ! The flaw works by writing to memory the new content so you cannot write content longer than the original size. If you attempt to write "123456" to a file containing "456", it will write "123".
I recently installed Ubuntu 12.04.1 TLS on one of my servers running Windows Server 2008 R2, following a reboot BIOS was stuck with an error message indicated that no valid media was inserted that allowed it to boot.
I verified and re-verified boot order, no problem, hard drive was indeed detected and first in boot order. I put back the DVD reader and started the server with Ubuntu Live CD. I then noticed that the recently installed Ubuntu was indeed there and well installed by mounting the partition. Issue was with the Grub, to repair it using Boot Repair from Ubuntu Live CD: - Connect to the internet. - Open a terminal, add the repository and install boot-repair.
sudo add-apt-repository ppa:yannubuntu/boot-repair
sudo apt-get update sudo apt-get install boot-repair - Then start Boot Repair and choose ”Recommended repair”. - Remove the Live CD and reboot the computer, it will start correctly on the hard drive. |
Archives
July 2021
Categories
All
|
 RSS Feed
RSS Feed